|
|
Back to Home Page Back to Toxic Waste
Below is a copy of the relevant portion of editorial from TCP # 27 with more material and references following that. The new material will be up-dated as more information is uncovered on this subject. It is astounding how much is to be found! Every new item seems to lead to two more.
|
Government
Shame in internet interference! Something I’ve suspected for sometime now, made the news last month. It seemed to me that Australian Customs Service, among other government services, were active in attempting to control content on the web. The “Wikipedia” (an on line reference source) page on Australian Customs was so blatant it had a label on the entry (since removed) stating that it read like an advertisement and requested an independent edit. I couldn't prove it but now anyone can thanks to a young Cal Tech Graduate, Virgil Griffith, who created a program and web site released in August, that allows anyone to trace the entries and edits made to the web based encyclopaedia. Go to <www.wikiscanner.virgil.gr>. Our government was one of the most prolific with perhaps the stupidest, rudest edit discovered so far, and where did it come from? The office of the Prime Minister and Cabinet. And the edit that took the prize? “Poo bum dicky wee wee.” No, I'm not kidding, this is your government at work. But in any case any entry that offended the government was likely to be vandalised including removing a reference to a liberal party member identified as “Captain Smirk”. Gee, who would that be? (Probably sits in Parliament near the Minister for Womb Control, bet you know who that is too) Our Department of Defence made over 5000 entries! I find that obscene. I was thinking of editing the Customs page in Wikipedia but frankly, I didn’t have the time. Our government is spending a fortune of our money to control information and re-write history just on this one web site. Consider the broader possibilities. It doesn’t end there. Last year, Richard Neville created a satirical web site, www.johnhowardpm.org that was bounced off the web within hours after it’s launch. The company that registered the domain name, MelbourneIT claims they were contacted by the office of the PM and asked to remove the site and they did. This censorship was improper and the site has since been restored but the controversy reveals the extent to which the government watches web content and how effective they are in censorship in spite of law. Interestingly, MelbourneIT was the web host for TCP at that time and inexplicably, the TCP IP address was changed without notification to TCP thus making it impossible to edit or publish on the site for some time. This lead TCP to change hosting and in fact remove the site from Australia. There is much more to this story, including allegations that our government may be involved in the political filtering of search results on web engines like Google. TCP is investigating these issues and will provide a web page with links to refer to sources for the statements above. |
|
References, additional facts and some speculation... What the "Australian" newspaper had to say about, "Poo Bum Dicky Wee Wee" Some of you may have heard of this news item but most I have talked to have not. Australian mainstream media is very kind to the government and these kinds of news items tend to not have the front page status they (in my opinion) deserve or would have if the opposition were the subject. The UK paper the "Telegraph" had more information. According to them, the office of the PM also edited in some very right wing religious drivel such as "Freemasonry is the work of Satan." and "Jesus is God." This is important in that it exposes the true workings and beliefs of the people involved as opposed to the fictional image they so stridently try to project. The denials of involvement by the PM seem absurd to TCP. This was an orchestrated endeavour. On the matter of Richard Neville and his site www.johnhowardpm.org, this one nearly went under the radar of the entire national media in spite of the fact it exposed horrendous violations of rights to free speech, free press and exposed melbourneIT as either a wimp or agent of the government. I speculate the governerment and melbourenIT may have a business relationship. This site by Australian Tim Longhurst seems well organised. According to Tim's report an agency called the "Australian High-tech Crime Centre" were involved in this as well as the PM's office. TCP had never heard of such an agency before this but it appears to be a case of a so-called "crime" unit being nothing more than a tax payer financed political hit and propaganda machine. While mainstream media in Australia were largely silent on this important issue, (Radio National an exception) overseas media were quite interested. This quote from international media organisation Reporters Without Borders on the subject; " Reporters Without Borders voiced shock today at the methods used by the office of Australian Prime Minister John Howard to censor parody website Johnhowardpm.org, on which political commentator Richard Neville posted a spoof speech by Howard about the presence of Australian troops in Iraq. The prime minister’s office had the website closed down on 14 March by going to Melbourne IT, the company that administers its domain name. “All the world’s leaders are subject to parody and the Australian prime minister should learn to live with it rather than banning it,” Reporters Without Borders said. “And anyway, to close down a website, a court order should be required, not just an administrative decision. This type of censorship is unacceptable in democracy, in which website managers have the same rights as those who run traditional media.” TCP will continue to research these matters and add information and references as they become available and time is found to publish. Update follows.... Lets go back to this "Australian High-Tech Crime Centre", what is this thing and what does it do? An examination of the web site reveals very little activity. A couple of bland bits of consumer advise posted, and media releases for the year total four items, one with two different names but the same document and all but but one copies of releases from a banking association (ABA). As a regular computer user I can certainly find no evidence of it's existence in practise. Criminal fraud attempts and solicitation of illegal substances, software etc, come to my email daily. According to the site that is their brief. I suggest then that they have failed miserably. In one of the rare instances when this organisation is mentioned on the web by other than it's own invention, the former director answers the question of "...why there haven't been any prosecutions to date, how come"? Otherwise the only instance where this shadowy agency has made news is in the case of the spectacular stuff up of the loss of a memory devise that contained the unencrypted banking details of some 3500 Australians. Not impressive. Because of lack of transparency in this organisation and apparent failure in it's stated mission it could be fair to ask if that mission has been accurately described. The capabilities and resources available are considerable. Is this agency little more than a domestic spy agency? Before you dismiss this query are paranoia consider the information above and this little background as well. Remember the Tampa? Children Overboard? According to this report, the government used a "top secret defence agency" to illegal monitor and record phone calls from the crew of Tampa to Australians to "form a political response to the crisis". The facts of this are: the government closely monitors web activity and employs large numbers of personnel to edit or construct material on the web to flatter or obfuscate as required to enhance the image and disguise the true nature of the governments activities. Further, the government is willing to pervert or even break the law to this end. How far can this go? Using the web as a sort of state sponsored terror devise is not knew. Even a whole country can be attacked as in the case of Estonia. In this report, the Russian government is alleged to have contracted with "botnets"to attack the system in Estonia to the point the entire country was crippled. What is a "botnet"? Have you had virus or function problems with your computer lately? Has it run very slow? Or crashed outright? It is very likely that your computer has been invaded. The invaders will take information from your computer but the main mission is to keep their software installed in your computer to enable them to use it. By spreading their virus among thousands, even millions of computers like yours, they can accumulate the computing power of several of the worlds largest mainframe units. Enough power that if directed with malice, can wreck a targeted system. This is a good place to insert another portion of the editorial as printed in TCP # 27; TCP web computers hacked but to no avail!
A sophisticated attack
was launched on the web computers of TCP. The attack began by
disabling the firewall settings in the OS and changing other
security settings within Windows XP. That computer was then loaded
with an assortment of Malware, spyware and virus. The next computer
to be connected to the poison wire went down in minutes upon
connection. Registry settings within the operating system were
changed externally! This is not amateur stuff. The computer was
reloaded with Windows XP, wiping all stored data in the process.
Three times the newly restored computer would be connected and
then wrecked as we watched in fascination. Very impressive. Though
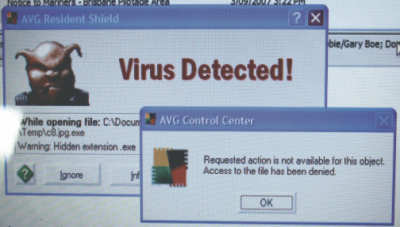
the anti-virus program ( I will point out that AVG is a respected
one), was helpless to remove the virus's, it did identify them.
A search of the hard drive then revealed the jpg images that
were embedded with the exe files. These images were not available
through any folder or document but hidden in the hard drive itself
and were absolutely unfamiliar. Soon after the above photo was
taken the anti-virus program was rendered inoperable.
Further notes on this matter. Though I have had numerous reports from other computer users in Australia of sudden virus and spyware difficulties with their computers last month, no report I have so far replicates the violence of the attack on TCP's computers except one, our server! And how did they do it? One possible answer is that if you have windows EX PRO you have a default setting in your "services"section that leaves your computer open to manipulation by someone on the other side of the world. This feature does not exist on XP home edition. For more information on this little bugger check this site. It is the best source of info on Windows I have found. This site dissects the system, item by item to explain and advise. I speculate that it may be possible that the attack on TCP was via a "botnet" type enterprise, though obviously of much smaller scale than Estonia. I think it is possible that the "Remote Registry" setting and the lack of an external firewall made it easy to do in our case. An interesting note to this is that the TCP web computers contain no valuable information, bank details or what not. Usually attacks of this kind are related to the gathering of information to sell. Ours was purely malicious. TCP has made it policy for some time to isolate production computers from those exposed to the web.
|